GENERAL INFORMATION SECURITY POLICY COCO TECHNOLOGICAL INVESTMENTS
CONTENT
1. SCOPE………………………………………………………………………………………………………………..3
2. DEFINITION OF TERMS………………………………………………………………………………………..3
3. ROLES AND RESPONSIBILITIES…………………………………………………………………………..4
3.1. INFORMATION SECURITY LEADER………………………………………………………………….4
3.2. INFORMATION SECURITY COMMITTEE…………………………………………………………..5
3.2.1. MEMBERS OF THE INFORMATION SECURITY COMMITTEE……………………..5
3.3. INTERNAL STAFF…………………………………………………………………………………………….5
3.4. EXTERNAL STAFF……………………………………………………………………………………………6
4. POLICIES……………………………………………………………………………………………………………..6
5. GENERAL GUIDELINES OF THE INFORMATION SECURITY POLICY
…………………………………………………………………………………………………………………………..6
6. OBJECTIVES……………………………………………………………………………………………………….8
7. RESPONSIBILITIES……………………………………………………………………………………………..8
8. COMPLIANCE……………………………………………………………………………………………………..8
9. VALIDITY…………………………………………………………………………………………………………….8
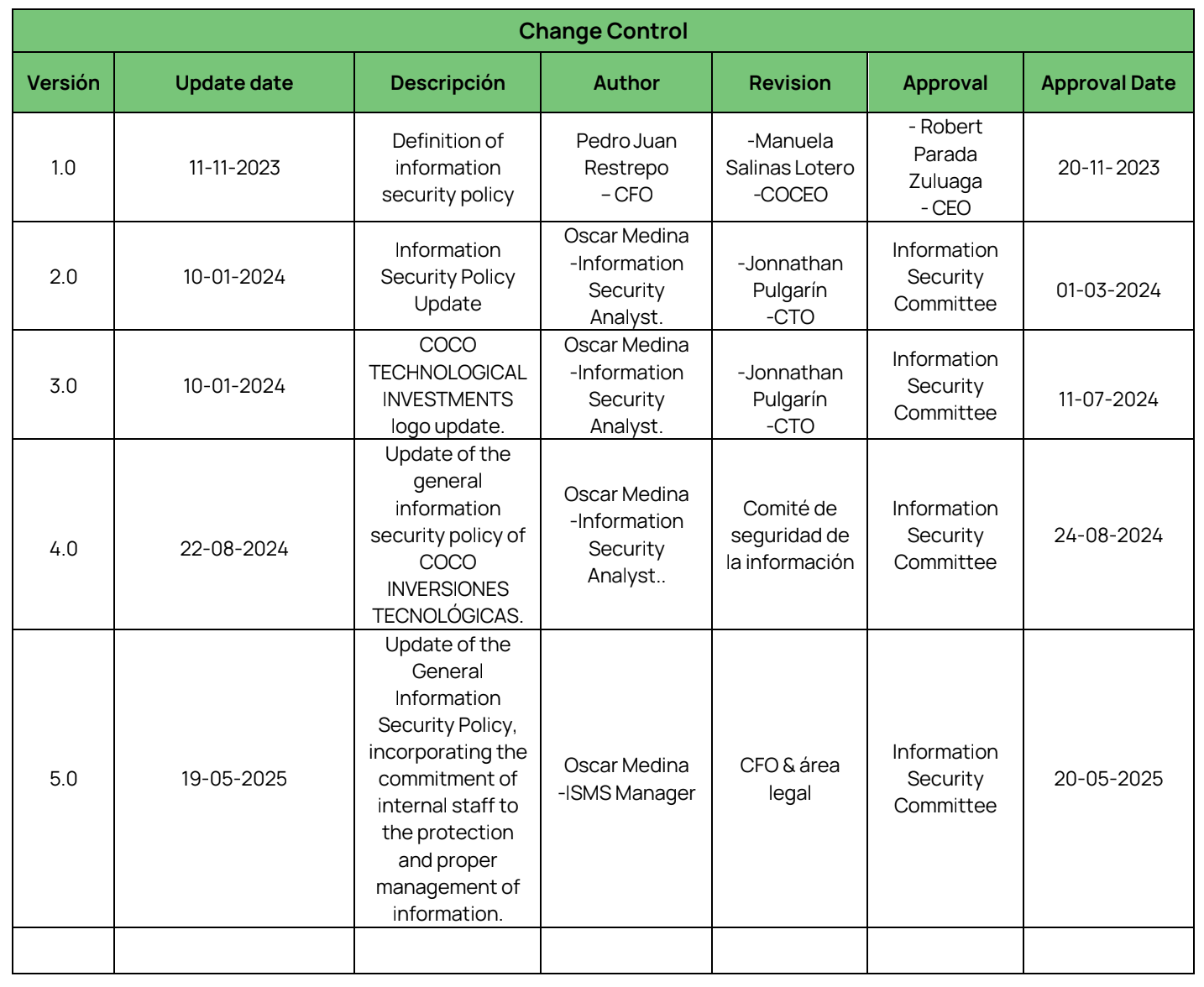
10. CHANGE CONTROL…………………………………………………………………………………………….9
1. SCOPE
This document has been developed by the Information Security department and has been approved by the CEO of COCO INVERSIONES TECNOLÓGICAS S.A.S. Compliance is mandatory for all corporate staff members, as well as third parties, suppliers, and contractors. This document establishes general guidelines to be followed in order to ensure information security, in accordance with the fundamental principles of confidentiality, integrity, and availability that have already been defined.
COCO INVERSIONES TECNOLÓGICAS S.A.S. is dedicated to providing specialized services in communication between healthcare institutions and patients through digital tools and artificial intelligence.
2. DEFINITION OF TERMS
For the purposes of this document, the following terms are defined:
a) Confidentiality
In accordance with the ISO/IEC 27001:2022 standard, confidentiality is defined as the quality that ensures information, in any medium, is only viewed and accessed by duly authorized individuals.
b) Integrity
As established by the ISO/IEC 27001:2013 standard, integrity is defined as the characteristic that ensures information, regardless of the medium in which it resides, is only modified by duly authorized individuals.
c) Availability
According to the ISO/IEC 27001:2022 standard, availability refers to the characteristic that ensures information in any medium is always accessible at the time it is needed for consultation or access.
d) Information Security Committee
Responsible for reviewing and proposing the current policy, as well as structuring, recommending, monitoring, and improving the Information Security Management System.
e) Control
As established by the NTP-ISO/IEC 17999:2007 standard, control is a risk management tool that encompasses administrative, technical, managerial, or legal regulations, procedures, standards, and organizational structures.
f) Information
Defined as an organized set of data in various forms, including text, numbers, graphics, among others, and which can be found in different media, such as magnetic storage, printed documents, computer screens, among other formats.
g) ISMS
Information Security Management System.
h) Assets
A company's assets are all the resources and properties owned by the company that
have economic value.
i) Politics
It is a set of principles or guidelines that guide decision-making and actions within an
organization to achieve specific objectives in a given area.
j) Internal Staff
Within this policy, internal staff shall be understood to include partners of COCO
INVERSIONES TECNOLÓGICAS S.A.S., as well as collaborators hired through an
employment contract, regardless of its type or type, and contractors linked through a
service provision contract or other type of contract.
k) External Personnel
Within this policy, external personnel shall be understood to include clients and
suppliers of COCO INVERSIONES TECNOLÓGICAS S.A.S., as well as any person of interest
who, due to their link or connection with the company, may have direct or indirect access
to the data managed by it.
3. ROLES AND RESPONSIBILITIES
3.1. INFORMATION SECURITY LEADER.
a) Implement the ISO 27001 standard – Information Security Management System (ISMS)
b) Identify information security and cybersecurity risks and threats
c) Design, develop, and execute mitigation strategies
d) Respond to customer requests related to evidence, records, audits, and progress of the information security management system
e) Support various business lines in handling information security incidents that impact the organization’s infrastructure and assets.
3.2. INFORMATION SECURITY COMMITTEE.
a) Review, evaluate, and approve the current scope of the ISMS of COCO INVERSIONES TECNOLÓGICAS S.A.S.
b) Review, evaluate, and approve the current version of the Information Security Policy of COCO INVERSIONES TECNOLÓGICAS S.A.S.
c) Review, evaluate, and approve the set of methodologies, standards, norms, and procedures that constitute the regulatory framework supporting this Information Security Policy.
d) Review, evaluate, and approve the measures to be executed in situations that threaten the security of COCO INVERSIONES TECNOLÓGICAS S.A.S.
3.2.1. MEMBERS OF THE INFORMATION SECURITY COMMITTEE
• CEO
• CO – CEO
• CMO – Commercial Leader
• CTO – Development Leader
• CFO – Administrative Leader
• ISL – Information Security Leader
3.3.INTERNAL STAFF
a) Accept in writing adherence to this policy and its supporting regulatory
framework.
b) Comply with the provisions of the regulatory framework of the COCO
INVERSIONES TECNOLÓGICAS S.A.S. ISMS.
c) Attend awareness and training sessions as required.
d) Report to the Information Security Leader situations that threaten the
e) Information Security of COCO INVERSIONES TECNOLÓGICAS S.A.S.
f) Participate in work meetings as required.
3.4. EXTERNAL STAFF
a) Accept in writing that they adhere to this policy and its supporting regulatory
framework.
b) Comply with the provisions of the ISMS regulatory framework of COCO INVERSIONES TECNOLÓGICAS S.A.S. as it pertains to their relationship with third parties.
4. POLICIES
For COCO INVERSIONES TECNOLÓGICAS S.A.S, information is one of the most important pillars in providing specialized communication services between healthcare institutions and patients through digital tools and artificial intelligence. For this reason, it is a priority that all our clients, collaborators, suppliers, contractors, partners, and stakeholders in general are aware of and accept our commitment as an organization to protect information, upholding the principles of Confidentiality, Integrity, and Availability. COCO INVERSIONES TECNOLÓGICAS S.A.S is committed to complying with all legal requirements and information security controls applicable to the company, as well as to continuously monitoring the Information Security Management System (ISMS) to improve and ensure its effectiveness.
5. GENERAL GUIDELINES OF THE INFORMATION SECURITY POLICY
It is essential that all individuals associated with COCO INVERSIONES TECNOLÓGICAS S.A.S — whether clients, collaborators, suppliers, contractors, partners, or stakeholders — take responsibility for safeguarding the corporate information to which they have access or that they process.
Their commitment lies in preventing the loss, alteration, destruction, or inappropriate use of such information.
1. For COCO INVERSIONES TECNOLÓGICAS S.A.S, it is vital to ensure the availability,
integrity, and confidentiality of each of the company’s assets, including:
• Information
• Collaborators
• Software applications
• Computer equipment
• Physical facilities
• Communication networks
• Auxiliary equipment
• IT systems
• Client databases
• Patient databases
2. COCO INVERSIONES TECNOLÓGICAS S.A.S is committed to managing, mitigating and
treating any risks that arise in the organization.
3. In the face of threats, such as regulatory changes and cybersecurity risks, we will
take proactive measures to mitigate risks and ensure the security and trust of our
customers.
4. In order to ensure the continuity of services, COCO INVERSIONES TECNOLÓGIAS
implements a business continuity plan.
5. In order to ensure the security of information, the specific policies stated below must
be complied with:
̈ GENERAL INFORMATION SECURITY POLICY
̈ ACCEPTABLE ASSET USE POLICY
̈ CORPORATE DESKTOP AND EQUIPMENT POLICY
̈ SARLAFT POLICY
̈ S-I INCIDENT AND EVENT MANAGEMENT POLICY
̈ PASSWORD POLICY
̈ BACKUP POLICY
̈ ID CARD POLICY
̈ EMAIL AND INTERNET POLICY
̈ SOFTWARE USE POLICY
̈ ACCESS CONTROL POLICY
̈ REMOTE WORK POLICY
̈ TELEWORKING POLICY
̈ PROJECT MANAGEMENT SECURITY POLICY
̈ INFORMATION LABELING AND CLASSIFICATION POLICY
̈ INFORMATION TRANSFER AND EXCHANGE POLICY
̈ INTELLECTUAL PROPERTY RIGHTS POLICY
̈ LOG AND AUDIT RECORD MANAGEMENT POLICY
̈ SYSTEM OVERLOAD POLICY
̈ ENCRYPTION POLICY
̈ SUPPLIER MANAGEMENT POLICY
6. Finally, in order to secure the information, compliance must be achieved with this
general information security policy and the specific policies established by COCO
INVERSIONES TECNOLÓGIAS, which will be reviewed twice a year at the end of each
semester or when significant changes occur.
6. GOALS
CULTURE: Train and raise awareness among all our collaborators and contractors on the importance of protecting the information managed by COCO INVERSIONES TECNOLÓGICAS, ensuring integrity, availability, and confidentiality.
INCIDENTS: Identify, analyze, and timely resolve information security incidents that occur within the company.
RISKS: Control, mitigate, and prevent risks associated with information security by identifying vulnerabilities and threats to the company’s most critical assets.
CONTINUITY: Ensure the continuity and availability of the organization’s processes.
SECURITY CONTROLS: Evaluate and monitor the controls, policies, and procedures implemented as part of the ISMS to ensure their proper functioning and the integrity of the system.
CONTINUOUS IMPROVEMENT: Establish a company-wide commitment to monitoring the entire information security management system.
7. RESPONSIBILITIES
The Information Security Department is responsible for managing the implementation
and ensuring compliance with this policy. It is also responsible for periodically reviewing,
updating, disseminating, raising awareness, and training staff. Failure to comply with this
policy will be considered a serious offense and will result in sanctions and/or warnings
previously established by the organization in its work regulations and/or relevant
documents. Depending on the severity of the violation, it may even result in the
termination of the existing relationship.
8. COMPLIANCE
This document will have to be reviewed and subsequently approved by the senior
management of COCO INVERSIONES TECNOLÓGICAS S.A.S.
9. VALIDITY
Permanent.
10. CHANGE CONTROL